 Photo from Getty Images
Photo from Getty Images
Originally Posted On: https://healthcareitsm.com/blog/delete-spam-office-365/
It builds and builds and creates anxiety, getting in the way of an otherwise productive workday. Spam emails often contain malicious links or attachments that can infect user computers with viruses, malware, or ransomware. Deleting specific spam, can help prevent security breaches and protect your user’s sensitive information.
Even though manually deleting spam is not email protection, sometimes emails still get through. It gets decision makers in situations where they may opt-out of getting additional email security. Let’s consider the top reasons companies may not have a certain level of cyber security set in place.
Top Reasons a Company Doesn’t Opt for More Email Security
Lack of awareness: Business owners are unaware of the importance of email security and the potential risks associated with insecure email communication or lack of email security training.
Complexity Concerns
Email security can be complex and require technical expertise. As a result, some individuals and organizations may not have the knowledge or resources to implement strong email security measures.
Cost
Some email security solutions can be expensive, and smaller organizations or individuals may not have the budget to invest in these solutions.
Healthcare ITSM Recommendation: Purchase add-on email security – For special pricing, contact us and ask us why we like Mimecast so much.
Our Favorite Email security platform.

mimecast awards
How to Delete Spam Using Microsoft Office 365 PowerShell
Tasks – Time 10 mins (First time 1 hour)
- Setup PowerShell
- Logging-in to O365 Exchange Using PowerShell
- Create a Compliance Search
- Delete the Emails Listed from the Compliance Search.
- Block Emails on O356 Spam Filter
1. Setup PowerShell
If this is your first time, please start with these steps. Skip if completed in the past.
Open PowerShell as an administrator
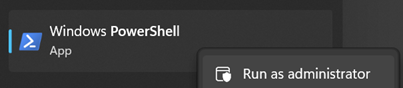
Run the command: set-executionpolicy remotesigned
Answer with: a
(This allows for scripting permission)
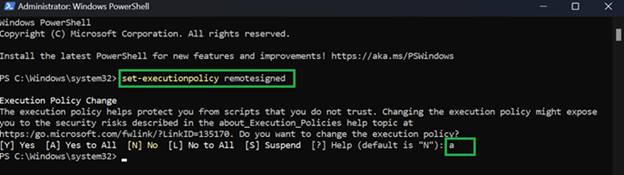
Run the Command: Import-Module ExchangeOnlineManagement
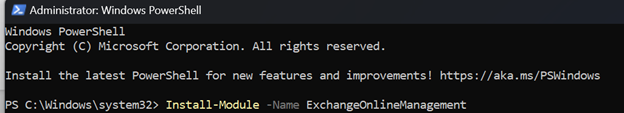
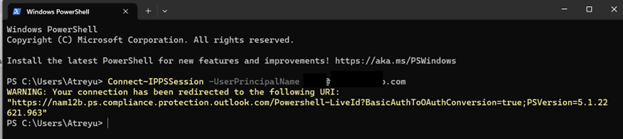
2. Logging-in to Exchange Using PowerShell
Run the Command: Connect-IPPSSession -UserPrincipalName email@domain.com
*Note: Change the email@domain.com to your email address
*Note: Email must have Office 365 Admin Access
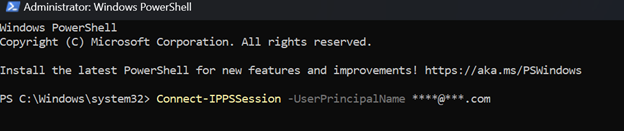
Sign-in to your account – If you have MFA setup this will prompt.
Wait for the log-in to complete!
3. Create a Compliance Search
Step 1
*Change the Highlighted parts in the script to fit your email deletion needs.
*Change the Highlighted parts in the script to fit your email deletion needs.
****Extreme Warning**** Be very specific, so you do not delete emails you don’t mean to delete. An example of a bad day: Delete all emails in the system that end with gmail.com
To learn more, see link below:
New-ComplianceSearch (ExchangePowerShell) | Microsoft Learn
Run the command:
$Search=New-ComplianceSearch -Name “UniqueName” -ExchangeLocation All -ContentMatchQuery ‘(From: Customerreply@mimecast.com)’
Start – ComplianceSearch -Identity $Search.Identity
![]()
* Example of multiple emails and/or subject
$Search=New-ComplianceSearch -Name “Phishing attempt” -ExchangeLocation All -ContentMatchQuery ‘(From:sendquick21@gmail.com) AND (Subject:”Inmailing System Interruption For anne ID:8205544455“)’
Start – ComplianceSearch -Identity $Search.Identity
Step 2
Check the Compliance Search to assess whether your search has collected what needs to be deleted.
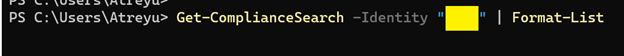
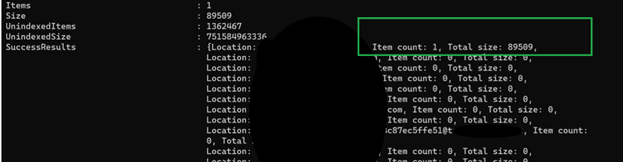
Run the command: Get-ComplianceSearch -Identity ” UniqueName” | Format-List
*Note: if there are many emails in the Tenant, please check the status by scrolling down and seeing the status.
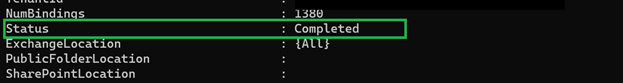
Once completed and the Results are confirmed, it’s time to Delete.
4. Delete the Emails Listed from Compliance Search
Run the Command: New-ComplianceSearchAction -SearchName ” UniqueName ” -Purge -PurgeType HardDelete
*Note: that it does take time to run, so be patient.
* There are different types of deletion in this command. Please see which one suits your needs.
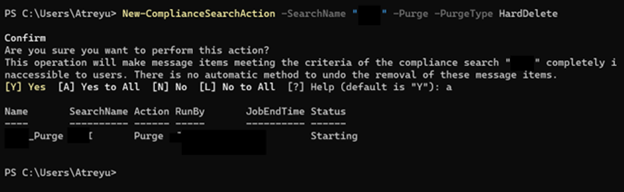
To check the status:
Run the command: Get-ComplianceSearchAction -Identity UniqueName_Purge | Format-List
5. Blocking Email on Office 365 Spam Filter
Log-in to : https://security.microsoft.com/antispam
1. Open Anti-Spam inbound policy (default)
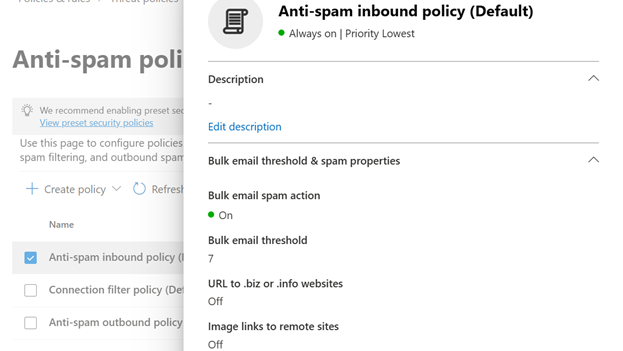
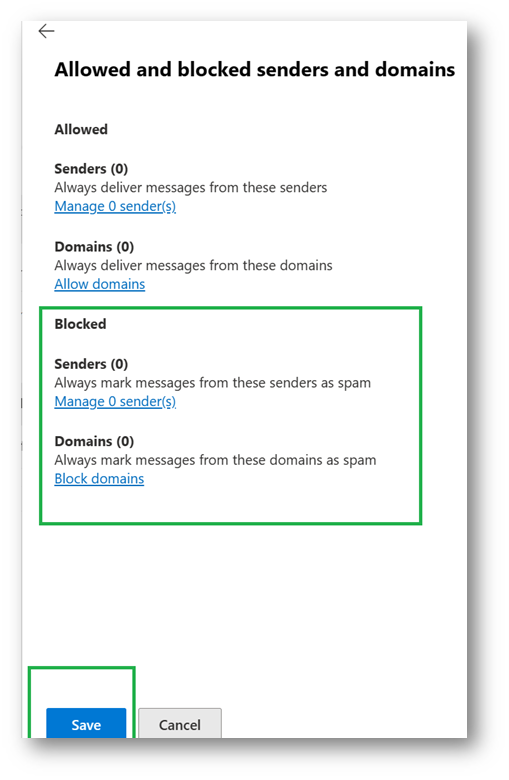
2. Scroll to the bottom and click: “Edit Allowed and blocked senders and domains”
3. Add the blocked sender or domain.
Healthcare Is Lacking Cyber Security
Cyber security threats are rising and are aimed to hit hospitals and healthcare providers. Consultation and help from an outsourced, expert team can save you and your company a lot of time and potential dollars.
Some things are common enough to quickly share throughout an office email:
- Do not click links or open attachments from unknown sources. This includes links and attachments in your personal email on company WiFi.
- Do not share your password or enter it in systems that you don’t recognize.
- Steer clear of online dangers while keeping a professional and acceptable technology use behavior.
- Report any issues immediately to your manager:
- Pop-ups or dangerous software running on your computer
- Files are not able to be opened anymore
- Computer shows a window asking you to call a phone number
- Files moved, disappeared, or copies of files moved to a different folder
- Lost or stolen technology
- Concerns or indicators of compromise
Further Reason for Concern
- According to the 2021 Verizon Data Breach Investigations Report, email-related incidents accounted for 36% of all breaches.
- According to the 2021 Cost of a Data Breach Report by IBM Security, malicious attacks were the most common cause of data breaches, with 52% of all incidents being caused by malicious attacks, and email attacks were the top vector for malicious attacks, accounting for 24% of incidents.
- According to a 2020 report by Cybersecurity Ventures, phishing attacks, which often use email as a delivery method, are expected to cost businesses $11.5 billion globally in 2021.
Contact Healthcare ITSM for Cyber Security and More
Unwanted emails clutter your inbox and get in the way of momentum during the workday. This is one example of how an easy fix can make a huge impact. We provide core services aligned with the IT service management framework. Whether you’re a startup or enterprise-level company providing healthcare, our holistic approach allows your organization the freedom to focus on core business.
In addition to cyber threats, we address needs related to help desk, information systems, projects and infrastructure, and IT finance. Contact us today to gain a better perspective of how we can help your healthcare business grow and succeed.













